Phishing (from English fishing - fishing) is an illegal act committed with the aim of forcing a person to share their confidential information, such as a password or credit card number. Like regular fishermen who use many methods to catch fish, cunning phishers also use a number of methods to "hook" their prey, but one phishing tactic is the most common. The victim receives an email or text message that poses as a person or organization that the victim trusts, such as a work colleague, a bank employee, or a representative of a government agency. When an unsuspecting recipient opens this email or message, they discover intimidating text, deliberately crafted to overwhelm common sense and instill fear. The text requires the victim to go to the website and immediately take certain actions in order to avoid danger or any serious consequences.
If the user “takes the bait” and follows the link, then he gets to a website that imitates one or another legitimate Internet resource. This website asks the user to "log in" using their account name and password. If he is gullible enough and agrees, then the entered data goes directly to the attackers, who then use it to steal confidential information or money from bank accounts; in addition, they may sell the obtained personal data on the black market.
"Phishing is the simplest form of cyberattack, yet one of the most dangerous and effective."
Unlike other threats found on the Internet, phishing does not require deep technical knowledge. Adam Kuyawa, director of Malwarebytes Labs, said: “Phishing is the simplest form of cyberattack, but one of the most dangerous and effective. This happens because the object of attack is the most powerful, but at the same time the most vulnerable computer in the world - the human mind. Phishing scammers do not try to take advantage of technical vulnerabilities in the operating system of the device, they resort to the methods of so-called social engineering. From Windows and iPhone to Mac and Android, no operating system is fully protected against phishing, no matter how powerful its antivirus tools are. In fact, attackers often resort to phishing, because cannot find any technical vulnerabilities. Why waste time cracking a layered security when you can trick a user into voluntarily revealing their data? In most cases, the weakest link in a system's security is not a bug buried deep in the code, but the user himself, who does not pay attention to the sender of the next e-mail.
History of phishing
The origin of the term "phishing" is fairly easy to trace. A phishing attack is in many ways similar to regular fishing. First you need to get a bait that can mislead the victim, and then cast the bait and wait until the “fish” starts to peck. In English, the combination of the words "fishing" (fishing) and "phony" (deception) led to the fact that the letter "f" was replaced by the digraph "ph", as a result, the term for malicious activities on the Internet acquired the spelling "phishing". However, some sources indicate that its origin may be somewhat different.
In the 1970s, a subculture developed that used a range of low-tech methods to hack telephone networks. These early hackers were called "phreaks" (phreakers), which is a combination of the words "phone" (telephone) and "freak" (fraudster). At that time, the number of computers connected to the network was small, so the purpose of phreaking was to make free international calls or calls to numbers not listed in phone books.
"Phishing is the simplest form of cyberattack, yet one of the most dangerous and effective."
Even before the term "phishing" was firmly established, phishing methods were described in detail in a report and presentation prepared in 1987 by Interex (International HP Users Group).
The use of the term begins in the mid-1990s, and its first mention is attributed to the notorious spammer and hacker Khan C Smith. In addition, the first case of public mention of the term "phishing" has survived on the Internet. It happened on January 2, 1996 on Usenet, on the AOHell newsgroup. At that time, America Online (AOL) was the largest Internet service provider, serving millions of connections daily.
Of course, the popularity of AOL has certainly made it a target for scammers. Hackers and distributors of pirated programs used its resources to exchange messages, as well as to carry out phishing attacks on the computers of law-abiding users. When AOL took action and shut down the AOHell group, the attackers adopted other methods. They sent messages to AOL users posing as AOL employees and asking users to verify their account information or give them their payment details. Eventually, the problem got so bad that AOL began adding warnings to every email, specifically stating that no AOL employee would ask for a user's password or payment details.
"Social media is becoming a prime target for phishing attacks."
With the advent of the 2000s, phishing scammers began to turn their attention to the vulnerabilities of electronic payment systems. Clients of banks and payment systems became increasingly victims of phishing, and in some cases, as subsequent investigation showed, the attackers were even able not only to accurately identify their victims, but also to find out which bank they used. Social networks have also become one of the main targets of phishing because of their attractiveness to scammers: personal information published on social networks is an excellent tool for identity theft.
Cybercriminals registered dozens of domains that imitated resources such as eBay and PayPal so gracefully that many not too attentive users simply did not notice the substitution. PayPal customers have received phishing emails (with links to a fake website) asking them to update their credit card number and other personal information. In September 2003, The Banker magazine (owned by The Financial Times Ltd.) reported on the first phishing attack against the bank.
In the mid-2000s, it was possible to order turnkey phishing malware on the black market. At the same time, hackers began to coordinate their actions in order to organize more and more sophisticated phishing attacks. It is difficult to estimate even approximate losses from successful phishing attacks: according to a 2007 report by Gartner, between August 2006 and August 2007, about 3,6 million adult users lost $3,2 billion.
"In 2013, 110 million credit card records and credentials belonging to Target customers were stolen."
In 2011, phishing scammers even allegedly found government sponsors when Chinese authorities launched an alleged phishing campaign that targeted Gmail accounts belonging to high-ranking officials and the military in the US and South Korea, as well as Chinese political activists.
Perhaps the most famous phishing attack was in 2013 when 110 million credit card records and credentials belonging to Target retail customers were stolen. The culprit was a compromised account of one subcontractor.
Even more infamous was a phishing attack launched in the first quarter of 2016 by the Fancy Bear hacker group (whose activities are associated with Russian special services and military intelligence). This attack targeted the email addresses of the US Democratic National Committee. In particular, John Podesta, Hillary Clinton's campaign manager for the 2016 presidential election, said that the attackers hacked into his Gmail account and stole correspondence because he fell for the oldest fraudulent trick: he received a phishing email warning that the password account has been compromised (so you need to "click here" to change it).
In 2017, a massive phishing attack on Google and Facebook was launched, forcing the accounting departments of these companies to transfer more than $100 million in total to the hackers' overseas bank accounts.
Types of Phishing Attacks
Despite numerous variations, a common feature of all phishing attacks is the use of forgery in order to appropriate certain values. Here are just a few of the main categories:
Spear phishing
While most phishing campaigns involve mass emailing to as many users as possible, spear phishing is targeted. In this way, attackers attack a specific individual or organization, often using tailored content that they believe will have the greatest impact on the victim. To carry out such an attack, it is necessary to conduct a thorough preparation in order to find out the names, positions, email addresses and other related information. Hackers turn the entire Internet upside down by comparing this information with all available information about the victim's job relations: they are interested, for example, in the names of colleagues and their responsibilities in the relevant organization. Having got all this data, malefactors make the plausible letter.
In particular, a phishing attack may target an employee whose duties include authorizing payments. The hackers send him a letter purporting to be from a high-ranking official of the organization, instructing him to make a large payment in favor of this person or in favor of the company's supplier (however, the attached malicious link does not lead to the payment system, but to a hacker website).
Spear phishing poses a significant risk to businesses (and governments) as it can lead to significant losses. Spear phishing accounted for 2016% of the cyberattacks they experienced during 38, according to a 2015 report from a multi-business study of the issue. For companies in the US that were victims of spear phishing, the average damage was $1,8 million per successful attack.
“A verbose phishing email from an unknown individual claiming to be a Nigerian prince is one of the earliest and longest-lived manifestations of such attacks.”
Clone phishing
This type of attack involves attackers copying (cloning) a previously delivered legitimate message that contains a link or attachment. The scammer then changes the links or attached files to malicious objects masquerading as real ones. Unsuspecting users click on a link or open an attachment, which is often enough for hackers to take control of the computer. The attackers can then masquerade as trusted senders and send similar emails on behalf of the victim to other users within the same organization.
Scam 419/Nigerian Letters
A verbose phishing email from an unknown person claiming to be a Nigerian prince is one of the earliest and longest-lived manifestations of such attacks. Wendy Zamora, Content Director at Malwarebytes Labs, said: “It is not uncommon for a phishing email to come from a Nigerian prince claiming to be a government employee or a member of the royal family and urgently needs help to transfer several million dollars out of Nigeria. Typically, such an email is marked as urgent or private, and its sender asks for a bank account number to which he could transfer money for safekeeping.
Sometimes classic Nigerian letters take on a rather amusing content. For example, in 2016, the British website Anorak reported that its editorial staff received an email from a certain Dr. Bakare Tunde, who introduced himself as an astronautics project manager working for the Nigerian National Space Agency. Dr. Tunde claimed that his cousin, Air Major Abaka Tunde, had been on the old Soviet space station for over 25 years. But for just $3 million, Roscosmos Corporation managers agreed to organize a flight of a manned spacecraft and return a Nigerian cosmonaut to Earth. The recipient of such a letter was required “only” to provide the details of his bank account so that the Nigerian specialists could transfer the necessary amount to their Russian colleagues. As a reward, Dr. Tunde promised to pay $600.
Randomly, this phishing attack also became known as the "419 scam". This number corresponds to the article number in the Nigerian penal code that punishes fraud.
Phone phishing
Phishing attacks can take place using a regular phone, in which case they are sometimes referred to as voice phishing or "vishing": the scammer calls his victim and pretends to be an employee of a local bank, police or tax office. He then intimidates the victim by reporting some problem and insisting that it needs to be resolved immediately, and for this you need to give him bank account details or pay a fine. Typically, scammers require you to transfer money by bank transfer or using a prepaid card so that they cannot be traced.
SMS phishing (or "smishing") is the evil twin of vishing, performing the same scams, but only through SMS messages (sometimes adding malicious links to them).
“In an email, the recipient finds an offer that looks too good to be true.”
How to recognize a phishing attack?
Recognizing a phishing attack is not always easy, but a few simple tips, a little discipline and common sense will help you. Pay attention to everything that seems strange and unusual. Ask yourself if the context of the message is suspicious. Trust your intuition and don't let yourself be intimidated. Phishing attacks often use fear to stifle your ability to think straight.
Here are some more signs of phishing:
In an email, the recipient finds an offer that looks too good to be true. It may say that you won the lottery, received an expensive prize or some unique item.
- You know the sender of the message, but this is a person with whom you do not communicate. Even if you know the sender's name, but it does not belong to your regular contacts, this should already be suspicious - especially if the contents of the letter have nothing to do with your usual job duties. Similarly, it is worth considering if the "Cc" field indicates secondary recipients of the letter that you do not know at all, or a group of employees from other parts of your organization.
- The text of the message inspires fear. Be alert if the body of the email is threatening or disturbing and tends to create an atmosphere of urgency by urging you to take certain actions urgently, such as clicking on a link, before your account is blocked. Remember that responsible organizations never ask customers to transfer personal data over the Internet.
- The message contains unexpected or unusual attachments. These attachments may contain malware, ransomware, or other online threats.
- The post contains links that look weird. Even if your intuition did not reveal the signs described above, you still should not blindly trust the hyperlinks embedded in the letter. Hover over a link to see its real URL. Look closely to see if a barely noticeable garbled spelling of a well-known website has crept into the hyperlink - if so, then this is a clear sign of forgery. It is better to enter the URL manually than to click on a link embedded in the text.
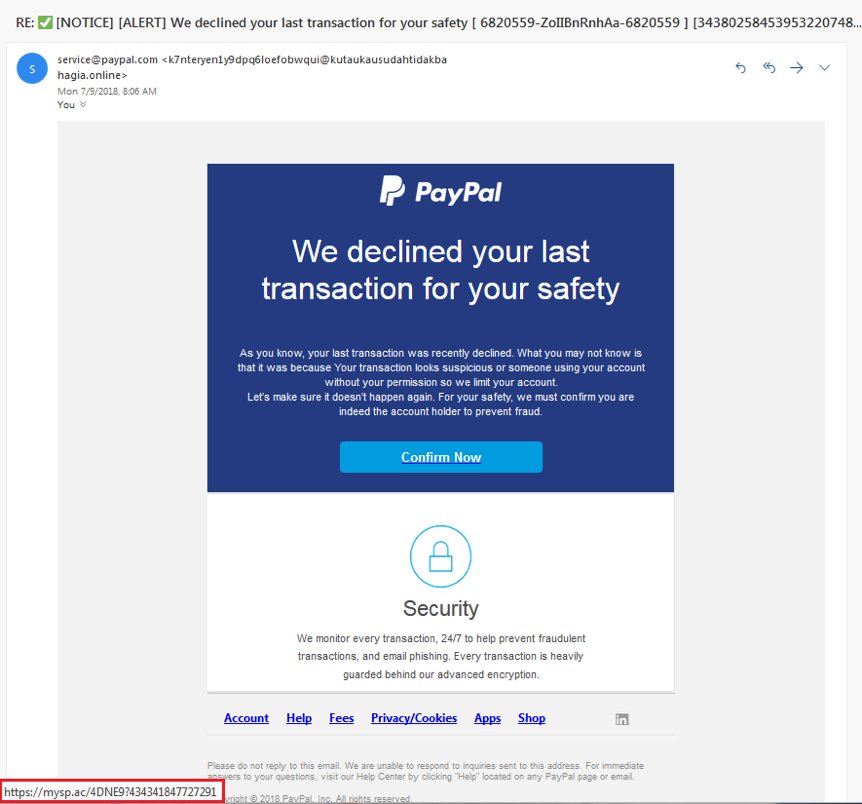
Here is an example of a phishing attack that mimics a message from the PayPal payment system asking you to click on the "Confirm Now" button. If you hover over this button, the browser will display the actual URL of the landing page - it is marked with a red rectangle.
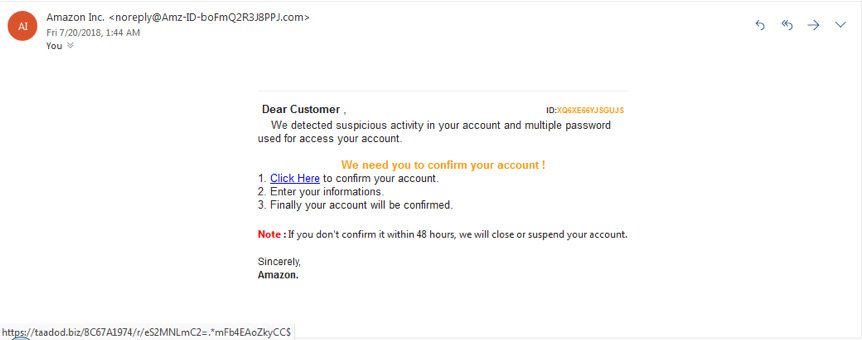
Here is an image of another phishing message masquerading as an Amazon notification. Pay attention to the threat to close the account if there is no response within 48 hours.
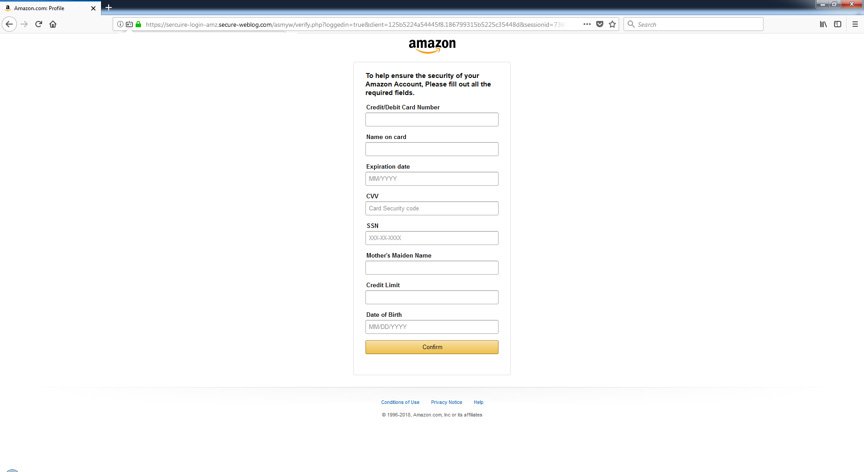
Clicking on the link leads you to this form, which offers you to provide the data that will open the way for attackers to steal your valuables.
How to protect yourself from phishing?
As discussed above, phishing is a threat that is equally likely to appear on a desktop computer, laptop, tablet or smartphone. Most Internet browsers check links for trustworthiness, but your first line of defense against phishing should be your ability to judge the situation. Learn to recognize the signs of phishing and stick to basic security principles when you check your email, read your Facebook posts, or play an online game.
Our colleague Adam Kuyava has formulated some of the most important rules that will help you not fall for the hook of scammers:
- Do not open emails from unknown senders.
- Only click on a link within an email if you know exactly where it leads.
- When you receive an email from a dubious sender, follow the attached link manually - enter the address of a legitimate website into the address bar of your browser using your keyboard, this will give you another layer of security.
- Check website digital certificates.
- If you are asked to disclose sensitive data, please make sure that the web page URL starts with "HTTPS" and not just "HTTP". The letter "S" stands for "secure" (secure), that is, the connection with this address is secure. However, this does not guarantee that the website is legitimate, but most legitimate websites use the HTTPS protocol due to its greater security. However, even legitimate websites using the HTTP protocol are vulnerable to hacker attacks.
- If you suspect that an email you received was sent by a scammer, enter the sender's name or text snippet into a search engine and you'll see if there are any phishing attacks associated with that email.
- Hover your mouse over the links to make sure they are trustworthy.
As always, we also recommend using a program that is able to resist malware. Most cybersecurity software is able to detect masquerading dangerous links and attachments, so your information won't fall into the wrong hands, even if you don't sense something is wrong in time.
All premium versions of Malwarebytes products provide reliable protection against phishing. They can recognize fraudulent sites, preventing you from opening them, even if you are sure that they are legitimate.
So stay vigilant, be careful and watch out for signs of a possible phishing attack.





















REPLY